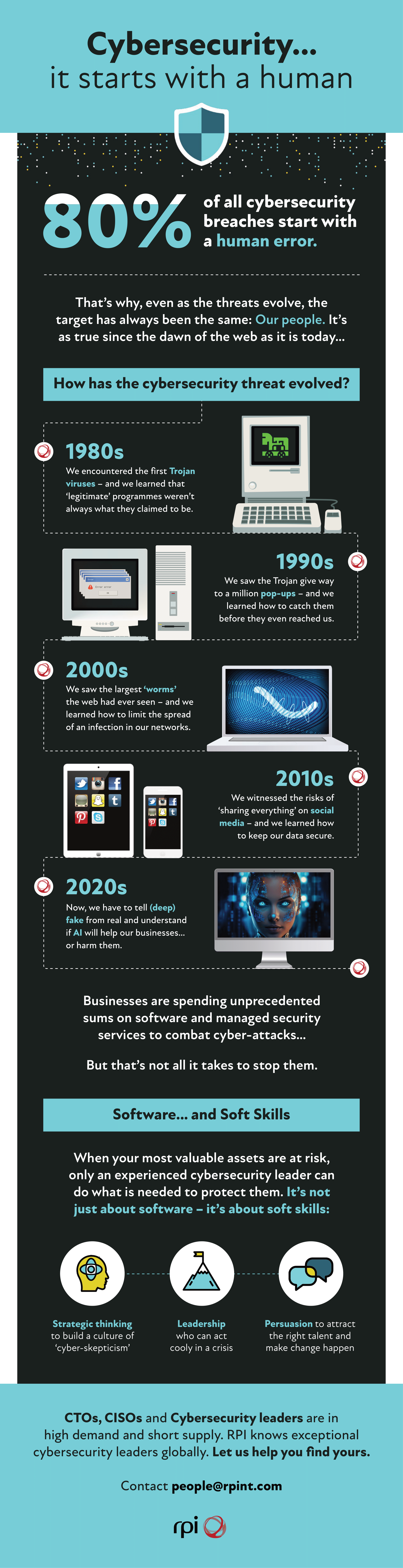
Believe it or not, human error is at the root of 80% of cybersecurity incidents.
This means that, in nearly 9 out of 10 cases, a criminal will have beaten a business’ defences by simply tricking an employee or taking advantage of a human oversight.
What’s more, those oversights are more common than you think.
When 43% of employees admit to having made an error that could cause a cybersecurity incident, it’s easy to imagine how that risk can spread far and wide.
Regardless of your industry or your location, you are a target for cybercriminals – and they will look to beat your defences by targeting your people.
There are 5 recent incidents that can teach us how attackers have exploited human error – and why the conversation needs to move from software solutions to people-focused strategies that recognise and address the risks that human error can cause.
The threats evolve… but the targets don’t
Cyber-crime has existed since before the term ‘cybersecurity’ entered our vocabulary.
From Trojan viruses to AI, we have seen cyber-criminals develop new and more ingenious ways to beat software – simply by getting people to lower their guard.
It should remind us that – no matter how much we try to create one - there is a single software solution for human error.
If you want to remember what cybercrime used to look like — and the new risks your company can expect to face in the near future—here’s our visual timeline.
5 industries in which human error has resulted in cyber-crime
Cybercrime takes many different forms – from data breaches and illicit money transfers and to leaks and ransomware. In no particular order, here are 5 industries that have been affected – all stemming from a single instance of human error.
1. Fintech and Financial Institutions
The Incident
The failed 2021 ‘Lazarus’ Heist saw state-backed North Korean hacker sattempt to steal $1 billion from the Central Bank of Bangladesh – and nearly succeed.
The Error
The 6-year operation started when bank employees simply clicked a suspicious email link from a criminal posing as a job candidate. This gave them the credentials they needed to access the SWIFT payment network and start requesting transfers from a ‘legitimate’ source.
The Lesson
Large financial institutions and adjacent services like payment providers are incredibly tempting targets –to such an extent that they don’t have to worry about ‘rogue’ hackers: but state-sanctioned ones, too.
2. Aviation
The Incident
In September 2023, a list of 3,200 of Airbus’ vendor partners was leaked onto a cybercrime forum. In this case, the leaker decided not to ask for a ransom – but threatened to target defence contractors next. Trust in the company would inevitably have been undermined for having lost sensitive partner data to malicious actors.
The Error
The criminal gained access to Airbus’ internal system using the credentials of an employee from a Turkish airline. These details were harvested when the employee attempted to install an ‘unauthorised version of Microsoft’s .NET framework’, which had allowed the criminal to install malware onto their computer.
The Lesson
While the ‘trigger’ was the employee attempting to download a malicious programme, this incident is a reminder of how aviation interconnects with so many other moving parts such as passenger processing and vendor management – which gives criminals the opportunity to use indirect (and possibly ‘weak’) entry points to reach more secure targets.
3. Telecoms
The Incident
In January 2023, 37 million records of T-Mobile customers were breached. The news of the breach resulted in a 1.5% decrease in its stock value, and eventually, a $350 million dollar settlement.
The Error
The ‘route-in’ was an ‘exposed’ API – which was left unsecured (and therefore, easy to manipulate). This let the criminal access to personal customer information through a third-party application channel.
The Lesson
Third-party APIs put access to your telecoms customers' data (e.g. for advertising) in another party’s hands. While it can be simple to strengthen your own cyber-defenses, cybersecurity leaders increasingly have to audit their entire supply chain to ensure their partners can’t provide criminals with an ‘in’.
4. Datacentres
The Incident
In April 2023, Tiktok was subject to a Forbes ‘exposé’ detailing lax physical security practices at its Virginia-based data centres. It caused further PR trouble at a time when TikTok was already facing bans in some US states.
The Error(s)
In an attempt to significantly expand server-side data storage and processing, TikTok was found to have cut corners. It regularly failed to monitor employee and third parties visiting their physical premises, which lead to unauthorised flash drives being found, hard drives wiped or missing, and even illicit crypto mining.
The Lesson
Cybersecurity leaders will be aware of the threat of DNS and DDos attacks on data centres – but even experienced directors may overlook the risk posed by simple, low-tech methods that their sophisticated solutions don’t account for.
5. Cybersecurity
The Incident
The largest data breach of 2023 occurred, surprisingly, at a cyber-security service provider: Darkbeam. In this breach, 3.8 billion records (login details of customers) were accessed.
The Error
Simply, a database of customer records had been left in a data search and visualisation platform that had been left unprotected by an employee. This gave a criminal easy access to this data.
The Lesson
A business can entrust its cybersecurity to a third party, such as a managed cybersecurity provider. However, it’s the responsibility of that business to also audit, research and understand a provider’s services, which may help them determine if that provider is up to the task of protecting their data.
In summary… what do these attacks tell us?
In short, these attacks tell us that no matter how sophisticated a business’ cyber-defences may be – and no matter their industry or location – cyber-attacks can succeed if the attackers reach those in your company who aren’t protected by software and are unaware of the steps to take if they know they are being targeted.
Businesses, globally, are expected to invest $219 billion in cybersecurity measures by the end of this year – hoping to offset the estimated $8 trillion cost of damage caused by cyber-attacks.
It’s a necessary spend to combat a growing threat - however, no amount of spending on software or cybersecurity service providers can stop an unknowing employee from clicking a malware-ridden link in an email.
History has shown time and time again that cybercriminals will always find a new ‘route in’ before the technology to stop them catches up.
That’s why software and soft skills are what businesses need to build robust defences against cyber-attacks, and with an estimated 3.4 million cybersecurity job needed by 2030, demand on culture-changing CTOs and CISOs in particular will be extraordinary.
That’s why companies need to hire urgently, effectively and competitively to bring about the changes needed to combat the cyber-criminal threats facing them.
RPI has deep industry connections, decades of experience, and a global network to connect businesses with cybersecurity strategists – those who don’t just know what software is needed, but who have the soft skills to bring about a culture of change that will minimise the exposure of your employees to cybercrime.
Learn more about RPI’s here, or click here to talk about the C-Suite talent you need to drive your cybersecurity strategy forward.



